Sometimes, we may need hide our process from various programs in order to achieve specific objectives. For instance, we may want to hide our virus from antivirus software, or conceal our cheat from anti-cheat programs. There are lots of different approaches introduced by blogs in internet. In this article, I will introduce a few methods that I believe are both effective and relatively straightforward.
Unlink EPROCESS
First and foremost, I want to emphasize at the beginning of this section that this method is not effective. In fact, it may even lead to various problems. EPROCESS, which stands for PCB (Process Control Block) in windows system, has led some individuals to believe that by unlinking EPROCESS, a specific process can be hidden. While this might have been true in older versions of Windows, attempting to hide any process using this approach in newer versions will almost certainly result in BSOD (Blue Screen of Death).
|
|
And you have to recover this unlinked node before process exits. You can call this function by Process Callback.
|
|
Deny Open Process
This approach, using the hook of NtOpenProcess, is an outdated method like unlink eprocess. Althouth this method may not completely remove a specific process from taskmgr, many people deem that denying requests to open any process is another form of hide process. This is because no process can open the specific process or retrieve information about it. The implementation is relatively simple, but it requires bypassing PatchGuard, because this approach denies open process requests through inlinehook of NtOpenProcess.
|
|
Set Process PID
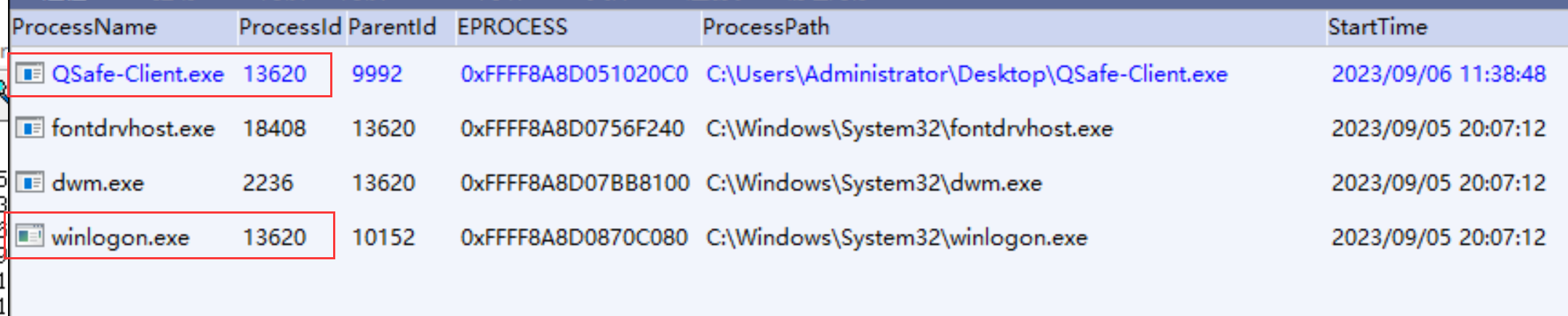
Not long ago, I discovered a method to hide process from a cheat sample. I couldn’t find this process from taskmgr, and I had seen this result by Ydark and NoOneArk.

Both Ydark and NoOneArk discovered that csrss.exe had been hidden, and they identified the real pid of this process. The question is: why can these ark-tools identify that this process has been hidden, but still retrieve its real pid.
The implementation is simple, too. This sample clears the pid of the process’s EPROCESS.pid variable. The following demo is the implementation method of the sample.
|
|
And we have two points to pay attention to:
- Setting EPROCESS.pid = 0 is not advisable, and it can somtimes cause the system to BSOD. Instead, I recommand considering assigning EPROCESS.pid a random value or using the pid of an existing process.
- We must recover EPROCESS.pid before the process exits.
Now, the question is that can we improve this approach to prevent ark-tools from retrieving the real pid, and even prevent detecting the presence of this hidden process? Before we can enhance this approach, it is crucial to understand how ark-tools can retrieve the real pid from a hidden process. As we are aware, each process consists of one or more threads, with these threads being represented by objects called ETHREAD in the kernel. ETHREAD records the thread’s pid and associated EPROCESS. Ark-tools enum all the threads and retrieve their pid and EPROCESS, and then compare the ETHREAD.pid with ETHREAD.EPROCESS.pid.
After comprehending the underlying principle behind how Ark-tools discover hidden process and retrieve their real pid, we can improve this approach to thwart Ark-tools from detecting our concealed process. One method to achieve this is by modifying the ETHREAD.Cid.UniqueProcess after setting EPROCESS.pid.
|
|
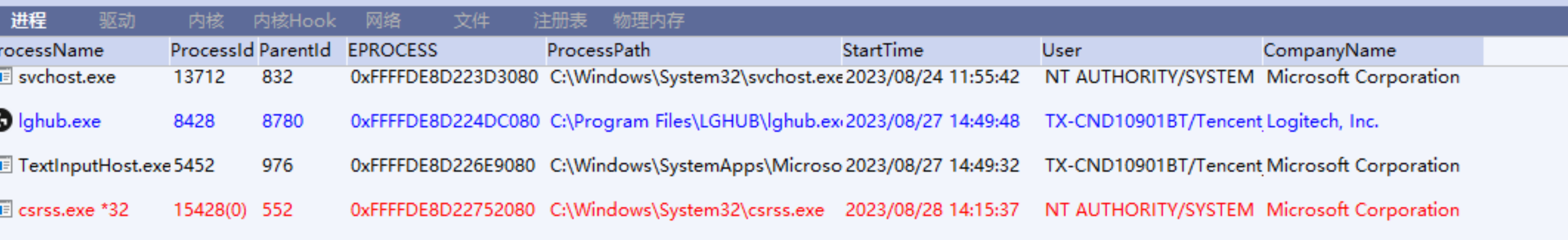
Using this method, Ydark can not find our hidden process and NoOneArk discover two processes which have the same pid.